Few things in the digital age are as common and annoying as spam calls. Whether you’re having a peaceful evening at home or in the middle of an important meeting, having uninvited telemarketers and scammers constantly ringing your phone can ruin your day and put your security and privacy in serious jeopardy. Thankfully, Stir/Shaken, a ground-breaking solution, is just around the corner and looks to take on this threat head-on. In this detailed blog, we’ll delve into the problems posed by spam calls, the potential risks they entail, and how Stir/Shaken is poised to change the game.
The Issue
Let’s be honest: spam calls are more than just an annoyance; they’re a major issue that millions of people experience globally. Spam calls can upset you and jeopardize your security and privacy, whether they are an unwanted sales pitch, a scam, or a malicious attempt to obtain your personal information. Furthermore, they can have serious repercussions in the real world, such as identity theft and financial loss, in addition to being a small annoyance. Spam calls persist despite efforts to filter and block them, partly because scammers can conceal their real identities and locations through spoofing techniques.
What is Stir/Shaken?
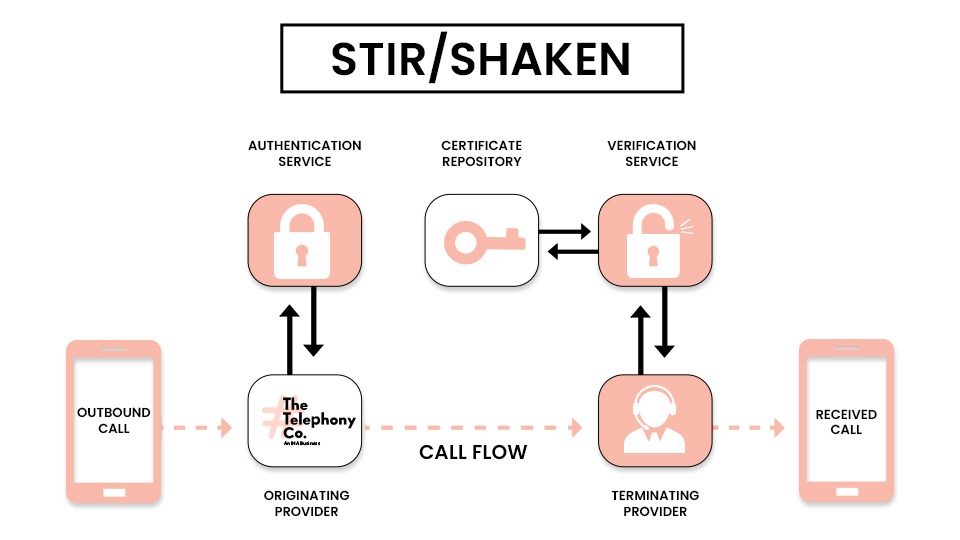
Fundamentally, Stir/Shaken is a cutting-edge technology that verifies the caller ID data sent with every call to combat the evil of spam calls. The namesake comes from two complimentary protocols: Signature-based Handling of Asserted Information Using toKENs (SHAKEN) and Secure Telephone Identity Revisited (STIR). When combined, these protocols provide a framework for confirming caller ID authenticity and preventing calls from being spoofed or altered while in transit. Let’s comprehend this in more detail.
STIR Secure Telephone Identity Revisited
The protocol known as STIR or Secure Telephone Identity Revisited, was develope to address the widespread problem of caller ID spoofing, which is a common method used by scammers and spammers to conceal their real identities and locations. Fundamentally, STIR offers a way to confirm the legitimacy of caller IDs by using cryptographic methods to authenticate and sign calls as they go over the phone network. The originating carrier creates a digital signature for each caller using cryptographic keys at the time of call initiation. This signature is sent with the call metadata and acts as a cryptographic proof of the call’s authenticity. The recipient’s carrier can then use the matching public key to confirm the authenticity of the signature after receiving it. The call is considered authentic and permitted to continue if the signature is verified; otherwise, it might be marked as suspicious or block completely.
With its strong and standardized framework for preventing caller ID spoofing and reestablishing network trust, STIR marks a breakthrough in caller ID authentication. Through the use of cryptography, STIR ensures that calls are authentic and callers cannot fabricate caller IDs. This reduces the possibility of fraudulent activity and improves the security of the telecommunications network as a whole.
SHAKEN: Signature-based Handling of Asserted Information Using toKENs
In addition to STIR, SHAKEN (Signature-based Handling of Asserted Information Using toKENs) offers a standardized framework for communicating call authentication status across the phone network. Expanding upon the cryptographic signatures produced by STIR, SHAKEN designates a “token” for every call, varying in level of authentication from “A” (completely authenticated) to “C” (unauthenticated). Based on the verification outcome, the originating carrier issues an appropriate token to an authenticated call using STIR. The call is then transmitted with this token embedd in the call metadata. Each carrier can check the token during a call’s journey across the phone network to determine the call’s authentication level. If necessary, they can implement call-blocking procedures for unauthenticated calls or show a verification indicator to the recipient.
Carriers can effortlessly exchange authentication information and guarantee consistent handling of calls across various networks thanks to SHAKEN, which offers a standardized mechanism for conveying the authentication status of calls. Carriers can effectively prevent caller ID spoofing, increase consumer trust, and improve transparency by integrating SHAKEN into their call-handling procedures.
Why Should You Know About Stir/Shaken?
It’s essential to comprehend Stir/Shaken for several reasons. First off, it gives customers more confidence in the legitimacy of incoming calls, which empowers them. You don’t have to worry about constantly wondering if a call is real because Stir/Shaken has authenticated the call and confirmed the caller ID. This can assist you in avoiding becoming a victim of con artists and scammers who trick their victims by using fake phone numbers.
Second, the amount of spam calls that bombard our phones every day could be significantly reduce with Stir/Shaken. Caller ID authentication makes it much more difficult for spammers to operate covertly and take advantage of phone network vulnerabilities. It also detects spoofing attempts. They’re therefore more likely to be found out and punished for their illegal activity, which will eventually make using our phones safer and more pleasurable. Moreover, Stir/Shaken is not just a theoretical idea—telecommunications companies all over the world are already putting it into practice. To effectively combat spam calls.
Conclusion:
To sum up, Stir/Shaken is a big advancement in the continuous fight against spam calls. It claims to make our phones safer, more secure, and more fun to use by verifying caller IDs and preventing spoofing. To take charge of our communication channels and safeguard ourselves from potential risks, consumers must comprehend Stir/Shaken. You can answer your phone with confidence the next time it rings because Stir/Shaken is working behind the scenes to keep you secure.